A Short History of
Cryptography
for Programmers
A Short History of
Cryptography
for Programmers
A Short History of
Cryptography
for Programmers

Gant Laborde

WHY!?
CRYPTOGRAPHY?
Why Cryptography?
It's here to stay



Why Cryptography?
It's cool


Why Cryptography?
It's part of a programmer's job

Ready!?
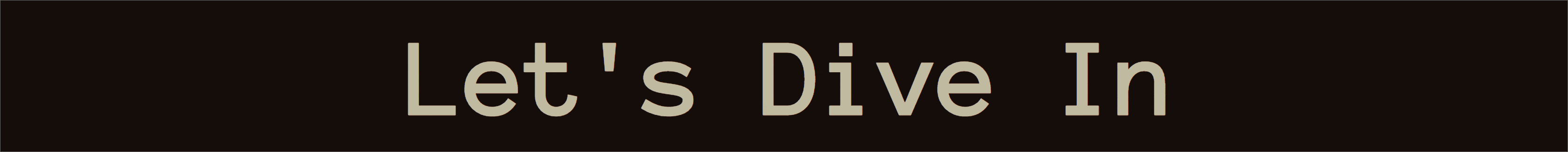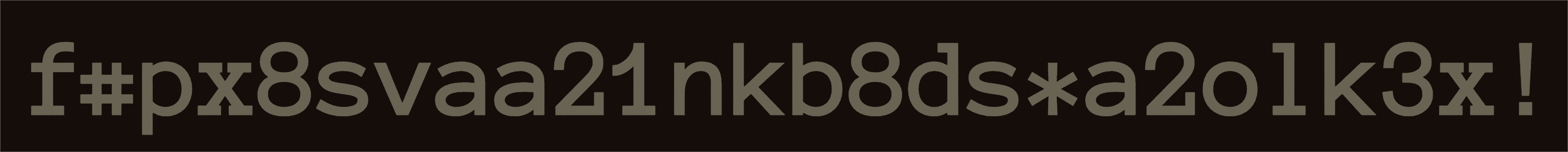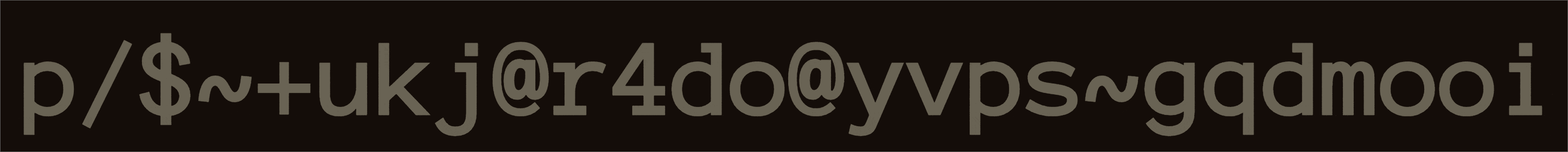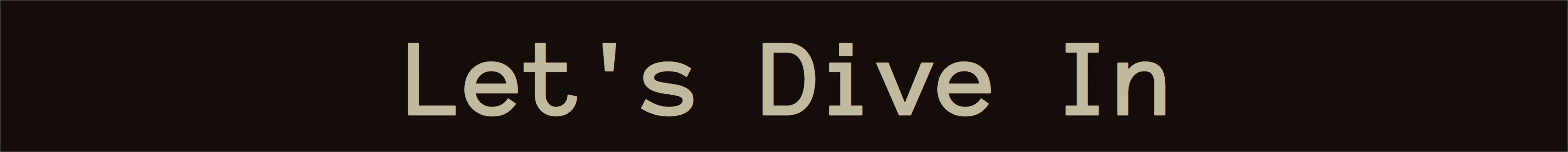
Ciphers are Old
1900 BC

The Oldest Keyed Cipher
Caesar / ROT

The Oldest Cipher
Substitution / Caesar / ROT

"If he had anything confidential to say, he wrote it in cipher, that is, by so changing the order of the letters of the alphabet, that not a word could be made out. If anyone wishes to decipher these, and get at their meaning, he must substitute the fourth letter of the alphabet, namely D, for A, and so with the others."
The Oldest Cipher
Substitution / Caesar / ROT
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
The Oldest Cipher
Substitution / Caesar / ROT
Can this become one encrypt/decrypt function?
YES!
Rotate the alphabet by 180 degrees
The Oldest Cipher
Substitution / Caesar / ROT
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
The Oldest Cipher
Substitution / Caesar / ROT
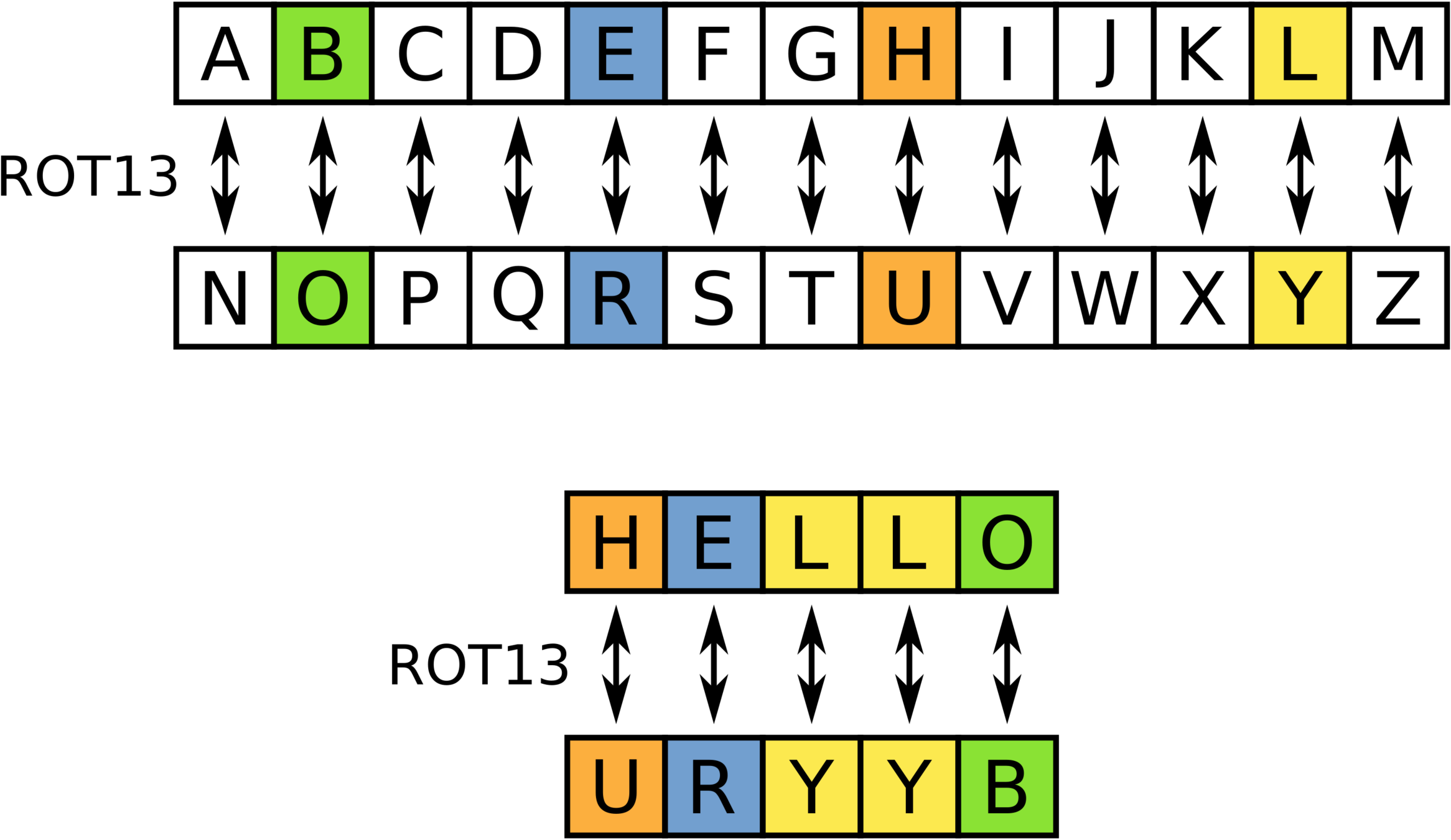
The Oldest Cipher
Substitution / Caesar / ROT
| Cipher | Encodes |
|---|---|
| ROT13 | Case insensitive 2-time letter only cipher (A-Z, a-z) |
| ROT5 | 2-time cipher for numbers (0-9) |
| ROT18 (13.5) | Case insensitive 2-time letters and numbers (0-9, A-Z, a-z) |
| ROT47 | All visible ASCII characters 2-time cipher |
The Oldest Cipher
Substitution / Caesar / ROT

The Oldest Cipher
Substitution / Caesar / ROT
3 Major Parts
- The Algorithm
- The Key
- The Ciphertext
The Oldest Cipher
Substitution / Caesar / ROT
What's the problem with Caesar (rotational)?
Really Simple Keyspace
The Oldest Cipher
Substitution / Caesar / ROT


Better Rotation
Vigenère cipher 1508

Better Rotation
Vigenère cipher 1508
Each letter has a corresponding rotation.

EVERY
1, 5, 8, 11, 14
FAMCM
Better Rotation
Vigenère cipher 1508

- Larger Key Space (up to message size)
- Frequency Analysis Resistant
Better Rotation
Vigenère cipher 1508
"The meeting is at the end of the street"
ROT13: GUR ZRRGVAT VF NG GUR RAQ BS GUR FBERRG
Vigenère with code 1508:
150 8150815 08 15 081 508 15 081 508150
UME UFJTQOL IA BY TPF JNL PK TPF XTZFJT
Remembering Numbers Sucks

1, 5, 8, 11, 14
?, ?, ?, ??, ??
Encoding Keys

| 1 | 2 | 3 | 4 | 5 | |
|---|---|---|---|---|---|
| 1 | a | b | c/k | d | e |
| 2 | f | g | h | i | j |
| 3 | l | m | n | o | p |
| 4 | q | r | s | t | u |
| 5 | v | w | x | y | z |
Polybius Square (knock Cipher)
Encoding Keys

| 1 | 2 | 3 | 4 | 5 | |
|---|---|---|---|---|---|
| 1 | i | n | f | t | e |
| 2 | r | d | a | b | c/k |
| 3 | g | h | j | l | m |
| 4 | o | p | q | s | u |
| 5 | v | w | x | y | z |
Polybius Square (knock Cipher)
Key Table Passphrase "Infinite Red"
Encoding Keys

Changing the position of a character depending on a secret is called a transposition cipher.
Transposition helps hide recognizable patterns in the result.
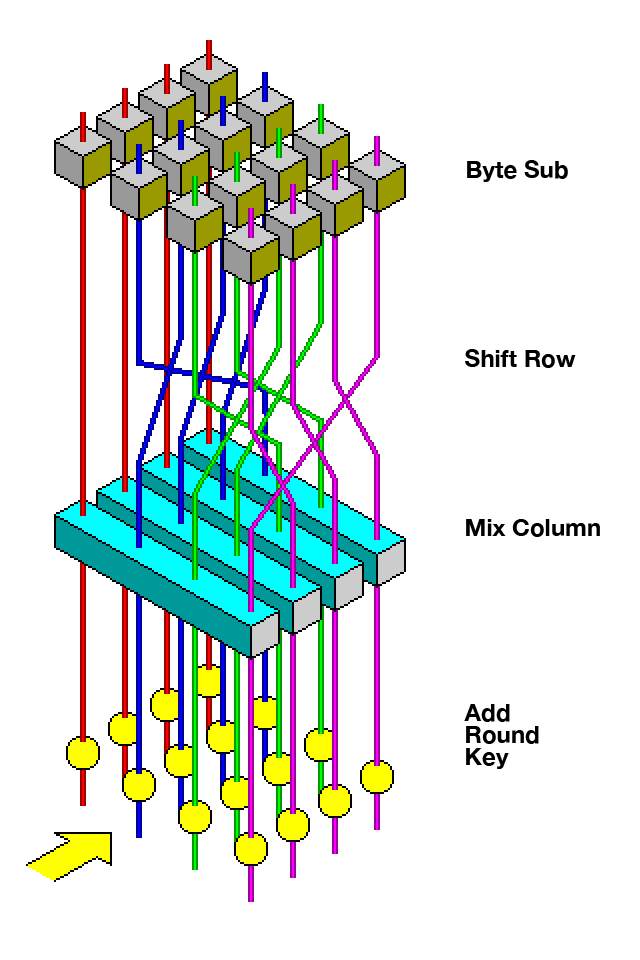
Stacking Confusion & Diffusion
Vigenère Cipher Key
Polybius Encoding
Message
Polybius Key Phrase
= Ciphertext
Do it again... and again... and again...
Jargon Alert
Symmetric Encryption Ciphers
- DES (Data Encryption Standard)
- AES (Advanced Encryption Standard) - Rijndael
- IDEA (International Data Encryption Algorithm)
- Blowfish (Like DES or IDEA)
- Rivest Cipher (RC5, RC6)
Digital Secrets
Encrypting your hard drive?
👍
Digital Secrets


Digital Secrets
Sharing secrets over the internet?

Digital Secrets
?
Ralph Merkle

Merkle's Insight

Whitfield Diffie & Martin Hellman

Digital Secrets
The Diffie-Hellman Key Exchange


Diffie-Hellman

p = 53
g = 18
x1 = 10
y1 = 38

p = 53
g = 18
x2 = 11
y2 = 48
48^10 mod 53
secret = 4
38^11 mod 53
secret = 4

We Want More

What can we do now!?
PUBLIC
KEY
CRYPTOGRAPHY
What can we do now!?

Public Key Crypto
Asymmetric Cryptography


Public Key
Private Key
What can we do now!?
-
Confidentiality
-
Authentication
-
Integrity
-
Nonrepudiation
All Good!?
Not Really... RSA Public Key was 100x's slower than DES

Cryptographic Hashing
Lots of things are easier one way.
- Opening a car door in tall grass vs closing it
- Square vs square root
- Shredding vs unshredding paper
- Hearing examples vs inventing examples
Cryptographic Hashing


New Tricks!
A Hash Gives You New Powers
- Identify if a file has been modified
- Verification across insecure channels
- Cryptocurrencies keeping anon
COOL NEW AUTH TRICKS!
Just Encrypt the Hash!




Fully Encrypt File
Sign/Encrypt Hash
One-Time Passwords

Jargon Alert
Asymmetric
- RSA
- ECC
Cryptographic Hashes
- MD5
- SHA-1 SHA-2
What can we do now!?


Authorization
Classic Way
Browser
Server
user/password
Cookie (Session ID)
Request + Session ID
Elevated Access Response
Scaled Authorization
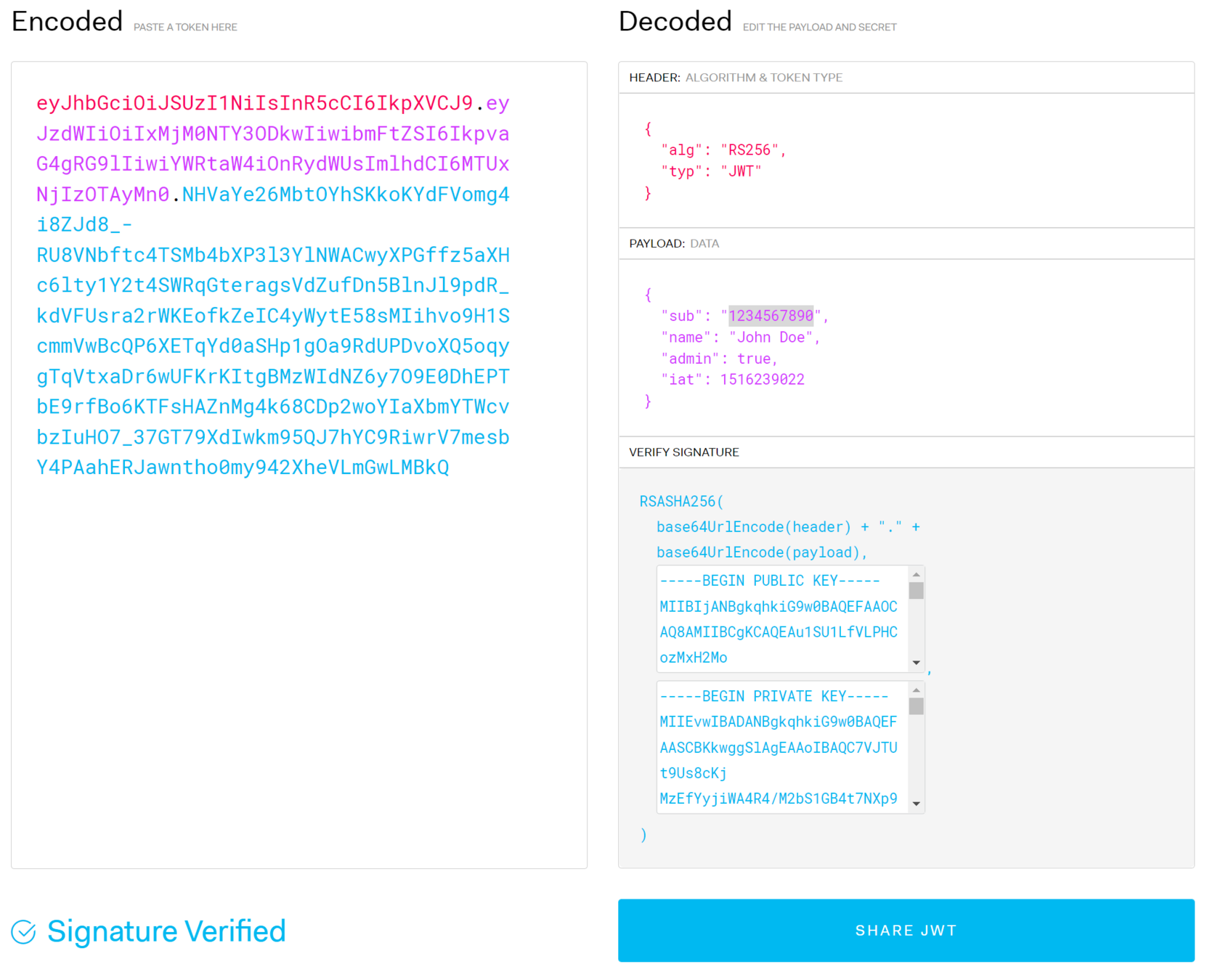
JWT - JSON Web Token
Browser
Auth Server
Any Service Server
user/password
signed JWT with secret
Request + JWT
Elevated Access Response
(No User DB
Needed)
Scaled Authorization


Scaled Authorization
Let's Review
- Confusion Diffusion Products
- Merkle's Insight
- Diffie-Hellman
- Public Key Cryptography
- Cryptographic Hasing
- JSON Web Token Authorization
Where do we go from here?
- Never rely on your own cryptographic algorithm
- Cryptography is actually kinda fun
- There's a whole world out there with techniques no one has considered yet. BE CURIOUS!
THANK YOU!
THANK YOU!
THANK YOU!

@GANTLABORDE